[Eine neue Perspektive auf die Akzeptanz von eHealth: Integration gesundheitsbezogener Einflussfaktoren in das Technologieakzeptanzmodell]
Robin Grashof 1Bernhard Breil 1
Myriam Lipprandt 2
1 Hochschule Niederrhein – University of Applied Sciences, Krefeld, Germany
2 Institute of Medical Informatics, RWTH Aachen University, Aachen, Germany
Zusammenfassung
Die Akzeptanz von eHealth-Lösungen durch Patienten ist nach wie vor begrenzt. Um besser zu verstehen, welche psychologischen Faktoren die Nutzung von Technologien beeinflussen, wird ein integratives Konzeptmodell vorgeschlagen, das das Technologieakzeptanzmodell (TAM) mit Elementen aus der Theorie der Schutzmotivation (PMT) und prozeduralen Aspekten des Gesundheitsverhaltens kombiniert. Das Modell beinhaltet eine Entscheidungsschleife, innerhalb der die Schutzmotivation die Nutzungsabsicht von eHealth-Lösungen beeinflusst. Es wird eine Kosten-Nutzen-Abschätzung durchgeführt, die sich auf die wahrgenommene Nützlichkeit von eHealth-Lösungen konzentriert. Die Entscheidungsschleife ermöglicht, die veränderte Gesundheitszustände und Nutzererfahrungen mit der Technologie zu berücksichtigen. Der hier dargelegte Ansatz zielt darauf ab, eine empirische Untersuchung zu ermöglichen, Modelle um gesundheitsspezifische Konstrukte zu erweitern und die Entwicklung adaptiver Bewertungsinstrumente zu unterstützen. Für eine empirische Validierung des Modells sind weitere Forschungsarbeiten erforderlich.
Schlüsselwörter
Technologieakzeptanz, Digital Health, wahrgenommene Bedrohung, Schutzmotivation, Gesundheitsverhalten
Introduction
According to Rose’s Prevention Paradox, an intervention can have a great impact on a population but a small impact on individuals [1]. The limited appeal of digital healthcare offerings warrants further investigation. In the Technology Acceptance Model (TAM), Attitude Toward Using is affected by Perceived Usefulness and the Perceived Ease of Use of the system, whereas the Ease of Use also impacts the Perceived Usefulness. The Attitude Toward Using influences the Behavioral Intention to Use, impacting the Actual System Use [2]. The Protection Motivation Theory (PMT) proposes Protection Motivation (PM) as the significant cause for security-related behavior (individuals’ actions to protects their health). PM arises from a process called Threat Appraisal, in which an individual evaluates its Perceived Threat Severity (how serious its consequences would be) and Perceived Threat Vulnerability (how likely they are to be affected), and weighs these factors against the intrinsic and extrinsic maladaptive rewards of (in)action (e.g., convenience, time saved). In parallel, Coping Appraisal encompasses the assessment of Perceived Response Efficacy (how effective the protective action is) and self-efficacy (individual’s confidence in performing it), against Perceived Response Costs (e.g., financial or effort-related burdens). Together, Threat and Coping Appraisal shape PM and thereby influence the intention to engage in security-related behaviors [3]. We want to consider factors influencing individual’s use of eHealth solutions. Particularly in the context of degenerative diseases, where patients’ needs, health status, and coping strategies evolve over time, longitudinal studies are crucial for understanding technology acceptance as a dynamic process. Yet, this specific intersection – acceptance trajectories in progressively worsening health conditions – remains largely underexplored in current research. To improve research, understanding and consideration of internal health-related factors in using eHealth solutions, we aim to derive a basic model with properties from existing models in technology acceptance and health psychology. Due to changing circumstances in dealing with diseases we also want to take account to temporal aspects. Synthesize a testable theoretical model based on established constructs, focusing on internal processes and facilitating the development of evaluation tools for health-related determinants of technology acceptance.
Methods
To clarify the conceptual nature of our model, we propose a hypothetical framework for operationalization. Our objective is to start with the established TAM to describe technology acceptance. To increase explained variance within the health context, we extend the model with specific health behavior-related factors and focus on theories giving specific internal constructs and processes from health behavior models. After Guo et al. demonstrated PMT to be adequate for research in eHealth-context [4], we adopt PMT components but more precisely and including use behavior. Since the importance of temporal aspects in health behavior change [5] and internet interventions have been demonstrated [6], we will include a dynamic component in form of a decision loop to consider change in decisions and behavior. Constructs as perceived vulnerability, health motivation, and decision feedback are mapped to measurable variables, based on established health behavior models. These could serve as the basis for future empirical testing.
Results
The proposed conceptual model is displayed in Figure 1 [Fig. 1]. As a base, we use the TAM with its fundamental coherences. PM is hypothesized to influence the Intention to Use Behavior, which also means a current decision against actual use. PM is affected by Perceived Threat Vulnerability and Perceived Threat Severity. We propose that users conduct a Cost-Benefit-Appraisal which influences the Protection Motivation. Here, we omit the efficacy constructs included in PMT and propose that efficacy of the eHealth solution is decisive for this appraisal. Hence, Perceived Usefulness exerts an influence on the appraisal which means that this factor is significant. After one decision loop, a user will develop experiential insights with or without the technology while changes in the health status may become apparent. Then, the user will run through the decision loop again, potentially informed by novel experiences or changed health-related circumstances as the starting point for the next loop, potentially with unlimited reiterations. Our model enables the formulation of longitudinal hypotheses about user engagement, such as how changing perceptions of vulnerability influence app usage over time.
Figure 1: Schematic figure of the proposed conceptional model. Outer bold lines frame one decision loop. Arrows display the effect direction. Components of original TAM are displayed with dotted lines. 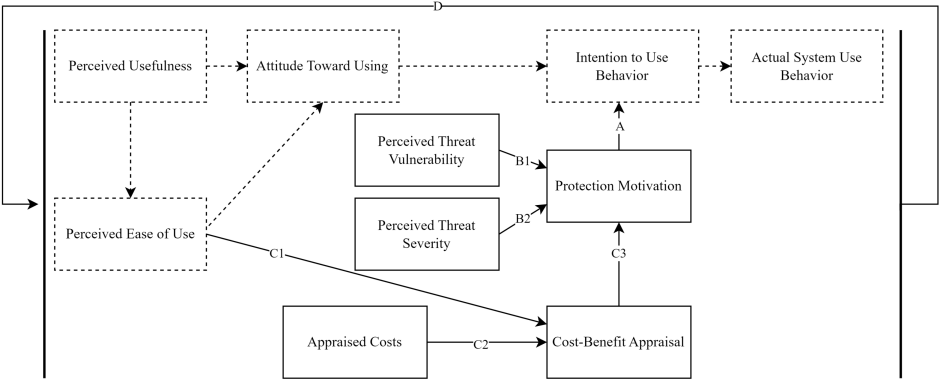
Effects enhancing TAM are labeled as follows: A = PM effecting Intention to Use Behavior; B1 and B2 = Perceived Threat effecting PM, C1, C2 and C3 =effects concerning Cost-Benefit Appraisal effecting PM; D = past decision loop(s) affecting next decision loop
Discussion
The information systems success model proposed an interdependence between usage intentions/system use and the user satisfaction [7]. Our model might itemize this relation for digital health contexts as it describes internal processes affecting use behavior as well as the system use behavior affecting future user satisfaction and future use intentions.
As the next step, the model needs empirical verification whereas its structure is incomplete due to its omission of external factors. While empirical testing remains future work, a viable methodological approach would involve a longitudinal study to capture feedback effects within the decision loop. It is possible to collect data via a survey using established questionnaires (e.g., [4]) and analyze it using hierarchical regression and structural equation models.
Notes
Competing interests
The authors declare that they have no competing interests.
References
[1] Rose G. Strategy of prevention: lessons from cardiovascular disease. Br Med J (Clin Res Ed). 1981 Jun 6;282(6279):1847-51. DOI: 10.1136/bmj.282.6279.1847[2] Davis FD. Perceived Usefulness, Perceived Ease of Use, and User Acceptance of Information Technology. MIS Quarterly. 1989 Sep;13(3):319. DOI: 10.2307/249008
[3] Balla J, Hagger MS. Protection motivation theory and health behaviour: conceptual review, discussion of limitations, and recommendations for best practice and future research. Health Psychol Rev. 2025 Mar;19(1):145-71. DOI: 10.1080/17437199.2024.2413011
[4] Guo X, Han X, Zhang X, Dang Y, Chen C. Investigating m-Health Acceptance from a Protection Motivation Theory Perspective: Gender and Age Differences. Telemed J E Health. 2015 Aug;21(8):661-9. DOI: 10.1089/tmj.2014.0166
[5] Prochaska JO, Velicer WF. The transtheoretical model of health behavior change. Am J Health Promot. 1997 Sep-Oct;12(1):38-48. DOI: 10.4278/0890-1171-12.1.38
[6] Ritterband LM, Thorndike FP, Cox DJ, Kovatchev BP, Gonder-Frederick LA. A behavior change model for internet interventions. Ann Behav Med. 2009 Aug;38(1):18-27. DOI: 10.1007/s12160-009-9133-4
[7] DeLone WH, McLean ER. Information Systems Success: The Quest for the Dependent Variable. Information Systems Research. 1992 Mar;3(1):60-95. DOI: 10.1287/isre.3.1.60




